cURL support for Apache
I guess allot of people know about cURL, it’s a pretty cool tool. For those who are unfamiliar with it, here is an extract from the Linux MAN pages.
"Curl is a tool to transfer data from or to a server, using one of the supported protocols (HTTP, HTTPS, FTP, FTPS, SCP,SFTP, TFTP, DICT, TELNET, LDAP or FILE). The command is designed to work without user interaction. Curl offers a busload of useful tricks like proxy support, user authentication, FTP upload, HTTP post, SSL connections, cookies, file transfer resume and more. The number of features will make your head spin!"
So here’s the thing, in the past when I have used cURL I did so by invoking it from the command line (or through some code like a python program). However I happened to be auditing a legacy phpMyAdmin install for which I found a ”Swekey” exploit online here. As you can see this is a php-based exploit (which uses cURL). For some reason I had assumed that my apache server would leverage the underlying OS functionality to make this exploit work but that was not the case. Let’s have a quick look at this problem and propose a quick fix…
(1) Replicate The Issue
Let’s download the php exploit from the link above and put it in our ”/var/www” directory…
(1) I’ll be using a meterpreter reverse tcp payload….
root@bt:~# ls -l /var/www/ total 36 drwxr-xr-x 10 www-data www-data 4096 2011-06-04 17:28 beef -rw-r--r-- 1 root root 1286 2011-11-08 16:31 evil.php -rw-r--r-- 1 root root 177 2011-06-04 17:36 index.html -rw-r--r-- 1 root root 20 2011-11-16 18:34 info.php -rw-r--r-- 1 root root 5586 2011-11-16 18:13 phpmyadmin_swekey_rci_exploit.php -rwxrwxrwx 1 root root 6435 2011-11-15 21:27 rds.c drwxr-xr-x 2 root root 4096 2011-06-04 17:35 wstool root@bt:~# /etc/init.d/apache2 start * Starting web server apache2
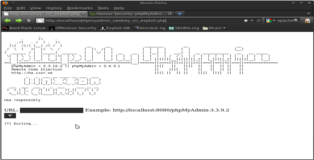
Ok so far so good. But what happens when we open this php exploit in our web browser (sorry forgot the screenshot). We are presented with the ASCII-art banner created by the author but underneath it there is an error “[!] Fatal error. Need cURL! [*] Exiting... ". So our apache server doesn’t support cURL, bummer…
(2) Fix the issue
Fixing this problem isn’t that difficult. It should take no more than 2 minutes :)). (1) Install a few requirements, (2) edit a configuration file and (3) restart apache…
root@bt:~# apt-get install curl libcurl3 libcurl3-dev php5-curl php5-mcrypt root@bt:~# kwrite /etc/php5/apache2/php.ini [Add this line to the configuration file: "extension=curl.so"] root@bt:~# /etc/init.d/apache2 restart * Restarting web server apache2 ... waiting
That’s it, after restarting the apache server we have cURL functionality. As we can see in the screenshot below when we reload the php-exploit in our browser it works perfectly. Time to pop a box ;))…