Game Over: XSS on FuzzySecurity
Today I’m bringing you a special post in the spirit of full disclosure, a DOM based XSS on FuzzySecurity. There are a couple of things I want to mention: (1) I found, exploited and fixed this bug; (2) before fixing it I took some time to determine if there was any actionable impact from an attackers perspective (there wasn't); (3) as far as I can tell from my logs no one else found or tried to exploit this vulnerability.
There are a couple of lessons to learn from this. You don't necessarily have oversight over code that you haven't written yourself, don't be lazy audit 3de party apps that you use. Never think your beyond falling victim to vulnerabilities.
Vulnerability Description / Impact
This XSS vulnerability was in jquery.prettyPhoto.js (v 3.1.3). Due to a lack of input validation on the hashRel it was possible to execute client side javascript in the context of the user browsing FuzzySecurity. In my case this resulted in a DOM based XSS.
This XSS is reflected, not stored which already mitigates the impact since the only way for an attacker to use it is to craft a link and send it to a victim. However since FuzzySecurity doesn't deal with any kind of session data the effect of the XSS is totally nullified.
Though this vulnerability is pretty harmless in my case any website that deals with client session data would have been at serious risk. An affected user could be tricked into performing sensitive actions within the context of their session or they could expose their cookie data to the attacker which would effectively allow the attacker to impersonate the affected user on the website.
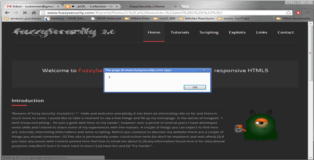
You can see an example of the attack below.
Sample Attack: /#!prettyPhoto/2,<a onclick="alert(1);">/ URL Encoded: /#!prettyPhoto/2,%3Ca%20onclick=%22alert%281%29;%22%3E/ POC Attack On FuzzySecurity: http://www.fuzzysecurity.com/#!prettyPhoto/2,%3Ca%20onclick=%22alert%281%29;%22%3E/
The Fix
Fixing the vulnerability was easy, all I needed to do was update PrettyPhoto to the latest revision. The bug was originally reported here and you can see a diff of the applied fix here.
Game Over!!