Inconspicuous Windows Backdoor
First things first, this is a novelty backdoor which is pretty inconspicuous and likely to remain undetected but at the same time it is difficult to imagine an attack scenario in which you would be able to implement this. My best guess would be that you have unsupervised access to a windows box and want to leave yourself a way in for later or just to play a prank on someone hehe.
Although I guess quite a few people know about this, I didn't and credit goes to Parvez Anwar from "greyhathacker" I can definitely recommend his website it has allot of really interesting articles.
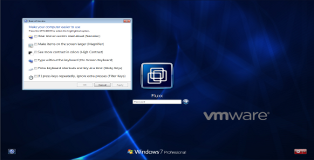
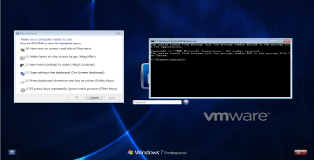
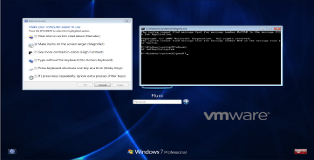
On to business! When logging into windows (Post WinXP) there is a "Ease of Access" menu, ask yourself have you ever opened that or used any of the tools in that menu? I'm guessing the answer is no but today we will finally find a use for it. You can see a screenshot of the menu below.
(1) Doing Things Manually
From the screenshot you can see the menu allows you to executes quite a few programs. The basic idea is that if we manage to change one of these programs with cmd we will be able to launch it as "system" without logging into windows. For our manual example we will be changing "Narrator.exe".
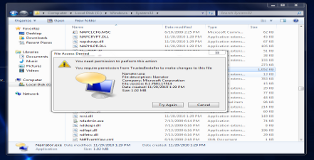
Log into windows, browse to "C:\Windows\System32\", find "Narrator.exe" and try to rename it. You should see a message like this popping up.
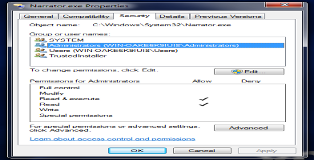
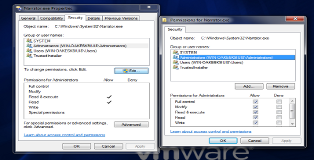
So clearly Windows is trying to be clever, it seems we only have read/execute privileges for this program. Ownership of the program belongs to a user called "TrustedInstaller" to prevent precisely what we are trying to do. Fortunately this access control feature can be disabled.
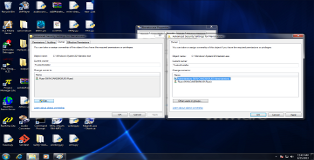
Go to Properties > Security > Advanced > Owner > Edit. There you can set the administrator as the new owner and save the settings. Once that is done go back to Properties > Security > Edit and give the administrator full access to the file.
You can now rename "Narrator.exe" to whatever you want and take a copy of "cmd.exe" and rename it to "Narrator.exe". Once you log-out and access the menu again cmd will pop up if you try to get the narrator to help you log in hehe.
(2) Auto Pwnd
So this all works out fine but you can see that modifying these files isn't exactly a speedy hit-and-run, however with a bit of google searching I discovered this whole process can be done with four terminal commands.
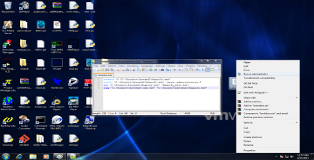
takeown /f "C:\Windows\System32\Magnify.exe" icacls "C:\Windows\System32\Magnify.exe" /grant administrators:F ren "C:\Windows\System32\Magnify.exe" "Magnify_back.exe" copy "C:\Windows\System32\cmd.exe" "C:\Windows\System32\Magnify.exe"
Just to show that this process works I have changed the file to be modified to “Magnify.exe”. Put these commands in a *.bat file > right-click run as administrator > Pwnd!!
I think everyone can agree this is a pretty neat backdoor not to mention that it probably won't get picked up because AV won't detect it and lets face it people never magnify their login screen. Like I said before figuring this into an attack vector isn't going to be easy but it's not impossible either. For instance (1) auto-deploy the script through a usb (2) log in through RDP (3) unauthenticated system access.